Post ElasticON: Cybersecurity & AI
Organizations face the daunting task of safeguarding their digital assets against a myriad of threats. Elastic Security emerges as a powerful solution, offering a modernized approach to security operations. At its core lies the Security Information and Event Management (SIEM) system, a key component empowering practitioners to detect and respond to threats proactively.
THE DETECTION CHALLENGE
Detecting threats is like finding a needle in a haystack, but what if the needle actively avoids detection? Distinguishing between normal and suspicious activities becomes crucial in this stage. Elastic Security tackles this challenge head-on, employing advanced techniques to discern anomalies and potential threats.
EMPOWERING ANALYSTS WITH DATA INSIGHTS
Elastic plays a pivotal role in empowering analysts to navigate the complex landscape of security data. With the ability to ingest data from hundreds of sources, Elastic Security allows practitioners to search, analyze, correlate, and identify patterns across various infrastructure components and cloud environments. The integration of Artificial Intelligence (AI) and Machine Learning (ML) augments the process, providing insights that guide analysts in their decision-making.

THE SECRET SAUCE: SIEM, ENDPOINT SECURITY, AND CLOUD SECURITY COMBINED
Elastic Security merges SIEM, security analytics, endpoint security, and cloud security into a unified solution. This integration forms the secret sauce, a potent weapon delivering comprehensive protection, investigation, and response capabilities to customers. Elastic Security Labs, with their proactive threat research, further enhances the platform by contributing valuable insights to the security community.
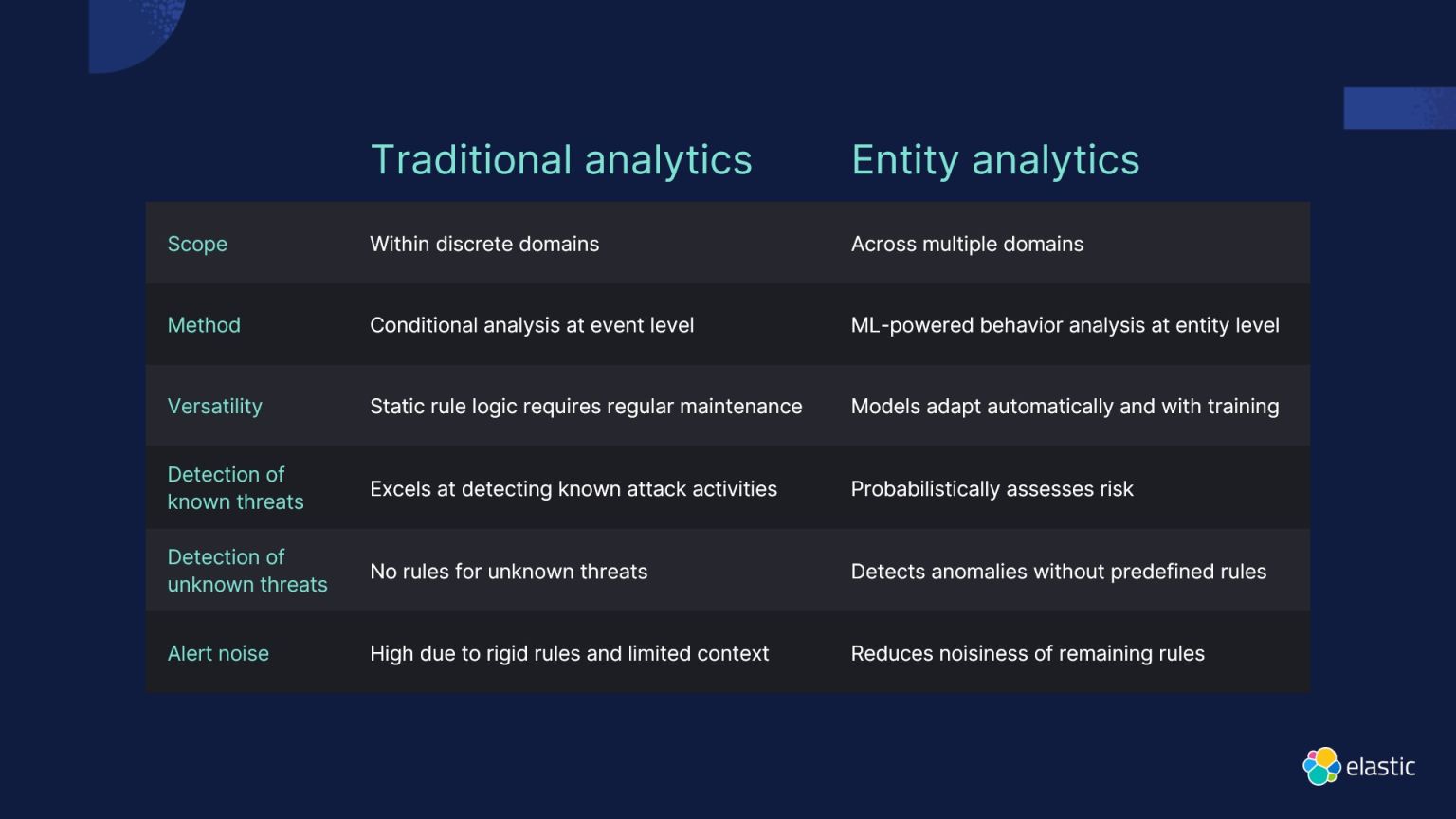
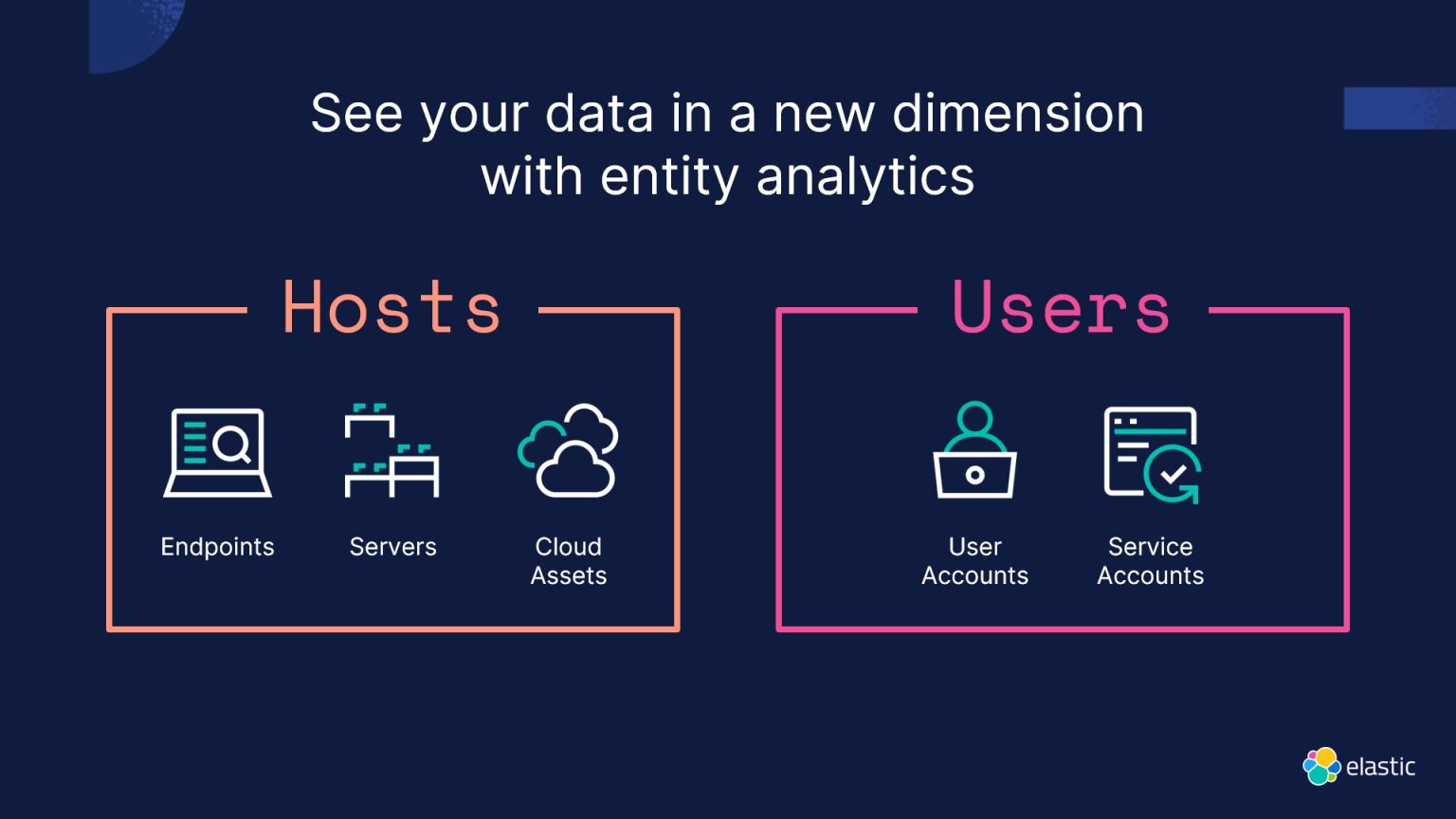
ENTITY ANALYTICS: UNDERSTANDING HOLISTIC BEHAVIOR
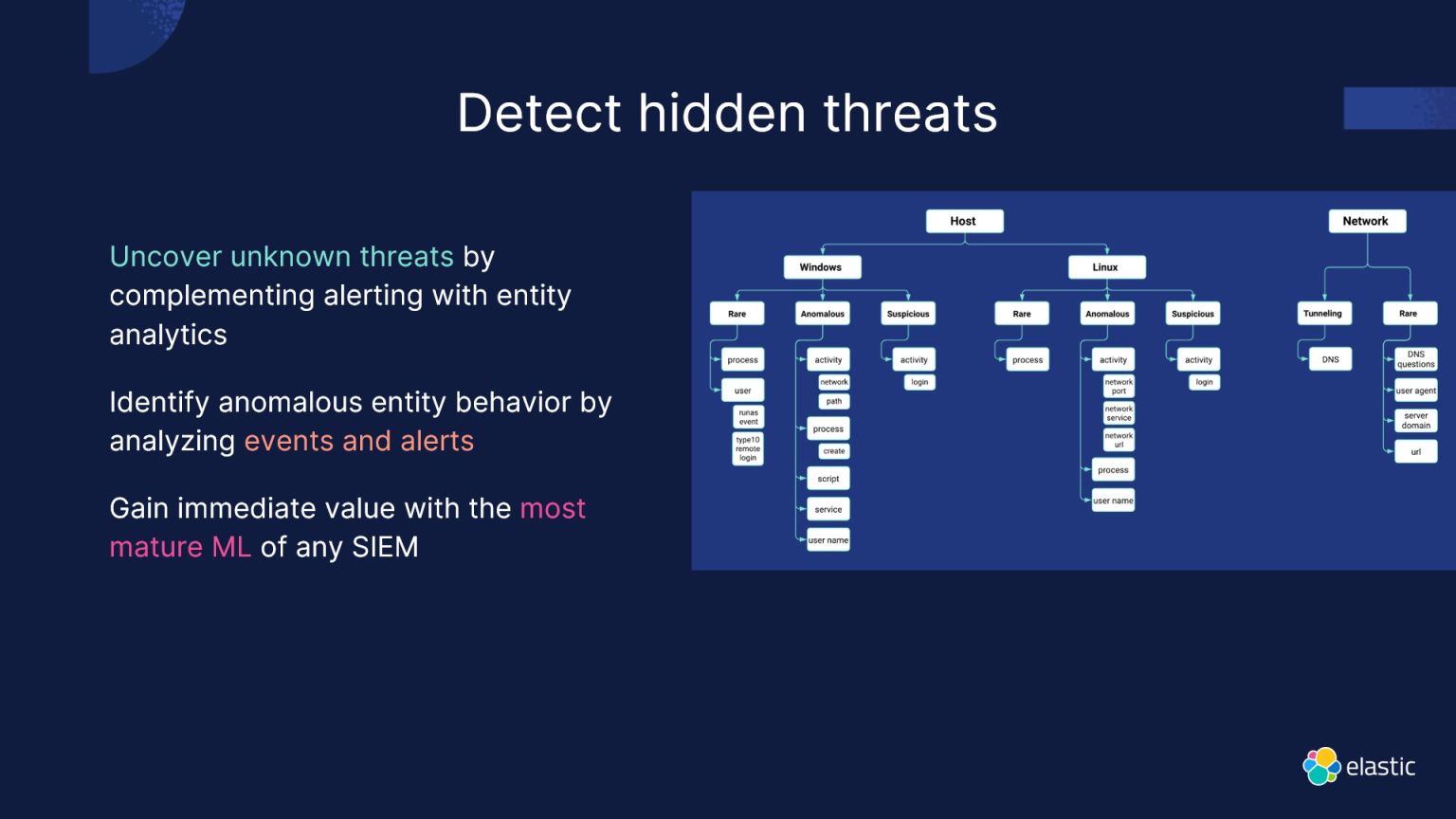
Entity analytics complements event-based alerting by focusing on understanding the behavior and interactions of entities within an environment. This goes beyond traditional event-based analytics, providing a holistic view of entity behavior through machine learning and statistical analysis. This approach enables the proactive detection of insider threats, system compromises, and data exfiltration.
THE POWER OF AUTOMATION
In a landscape where every moment counts, automation becomes a critical ally. Elastic Security incorporates automation to minimize the time between threat detection and investigation in cloud environments. With over 50 prebuilt machine learning jobs and use case packages, Elastic Security Labs significantly enhances the platform's ability to automatically block threats.
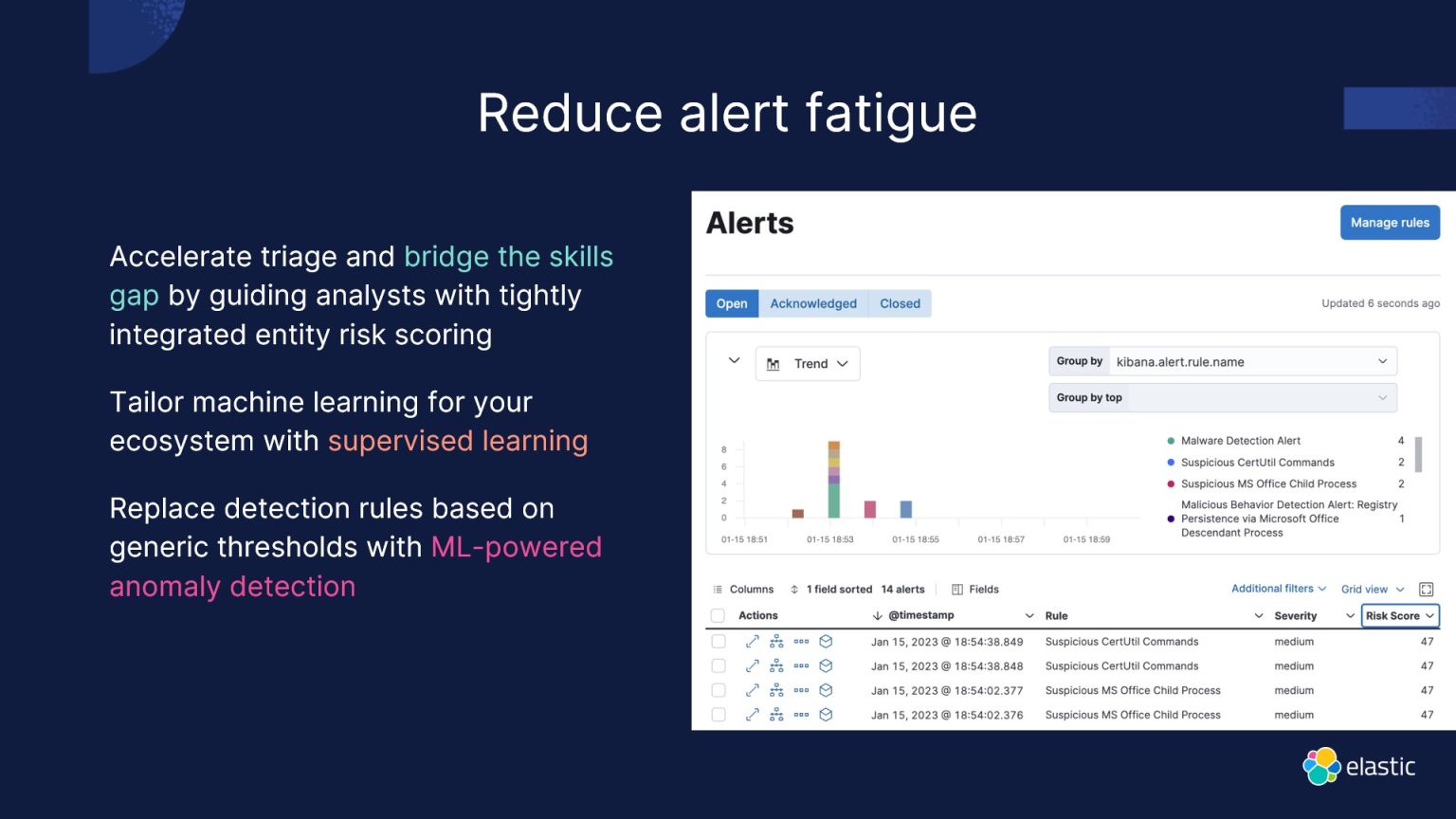
GENERATIVE AI REVOLUTIONIZING SECURITY ANALYTICS
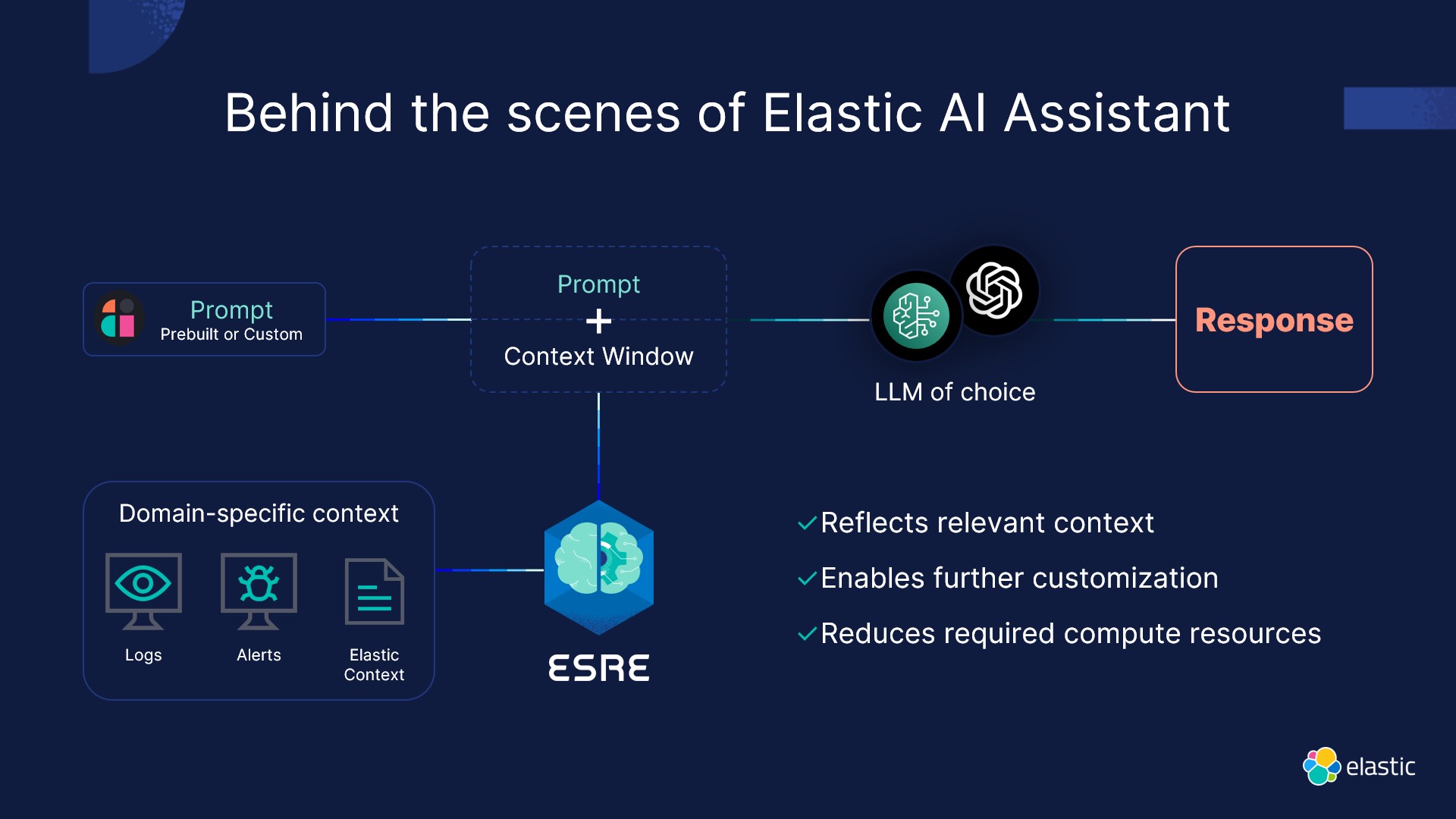
Elastic Security embraces the transformative power of generative AI, revolutionizing security analytics. This tool, powered by LLM (Large Language Models), allows users to bring in data from any source, facilitating proactive threat detection. Privacy concerns are addressed through data anonymization and role-based access control, ensuring secure usage of LLM.

AI AND ANALYTICS AT SCALE
Elastic's extensive capabilities for AI and analytics extend to processing large datasets at scale. With machine learning-based anomaly detection, automatic correlations, log categorization, and interactive chat-based investigations, Elastic Security provides a comprehensive suite of tools. Over 100 Out-of-the-Box (OOTB) open ML models offer customization for diverse data and use cases.

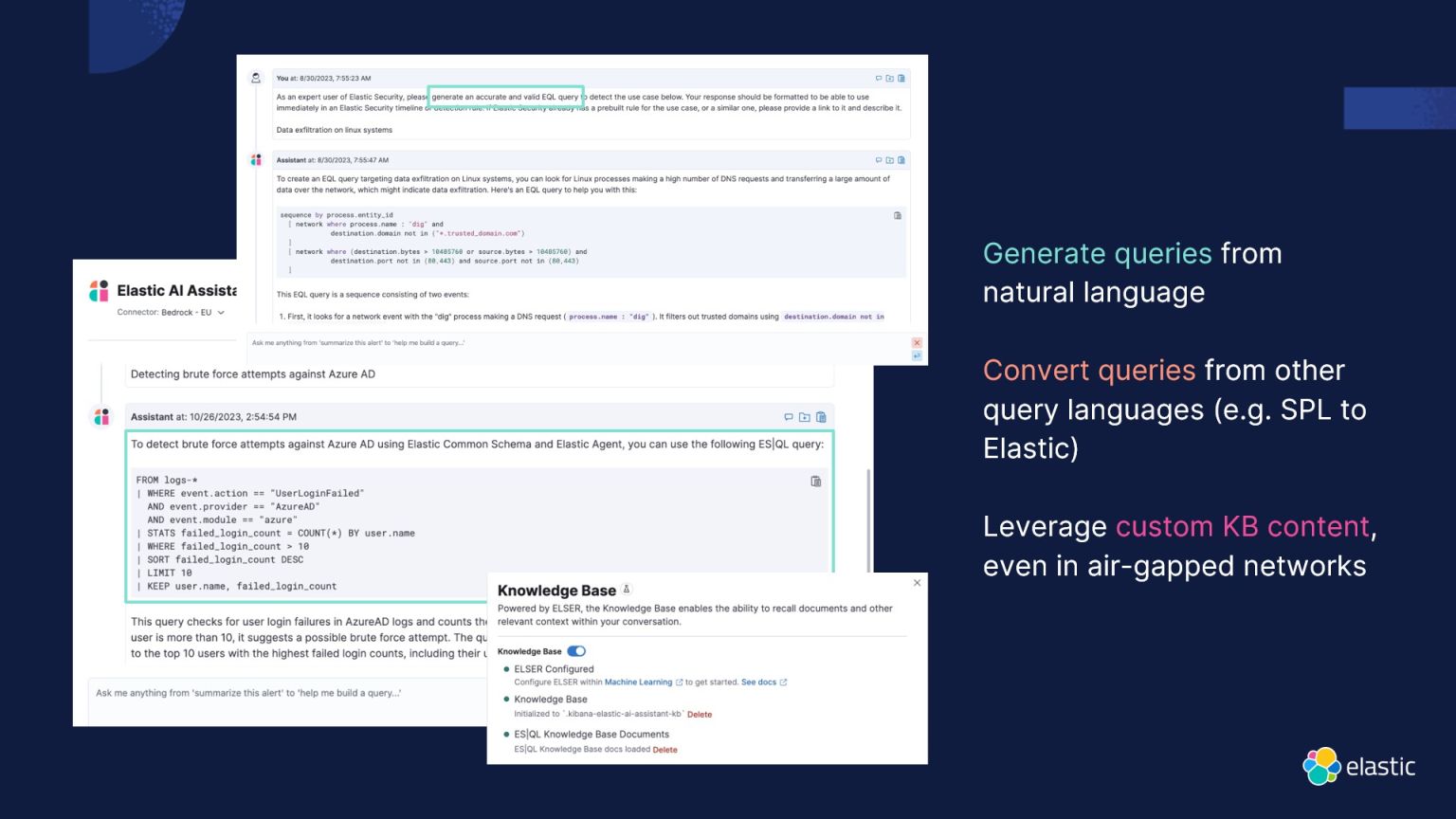
DEMOCRATIZING ACCESS TO DATA AND ANALYTICS
The democratization of data and analytics is a hallmark of Elastic Security. The platform's capabilities are not confined to data scientists alone; they are accessible to the entire organization. This inclusivity ensures that insights derived from AI and analytics are widely available, contributing to a more robust security posture.
In conclusion, Elastic Security stands as a transformative force in the realm of cybersecurity. By seamlessly integrating advanced technologies, proactive threat research, and a commitment to democratizing access to security insights, Elastic Security empowers organizations to stay one step ahead in the ongoing battle against cyber threats.
Contact us